Brief Descriptions of the Function of Each QEI Component
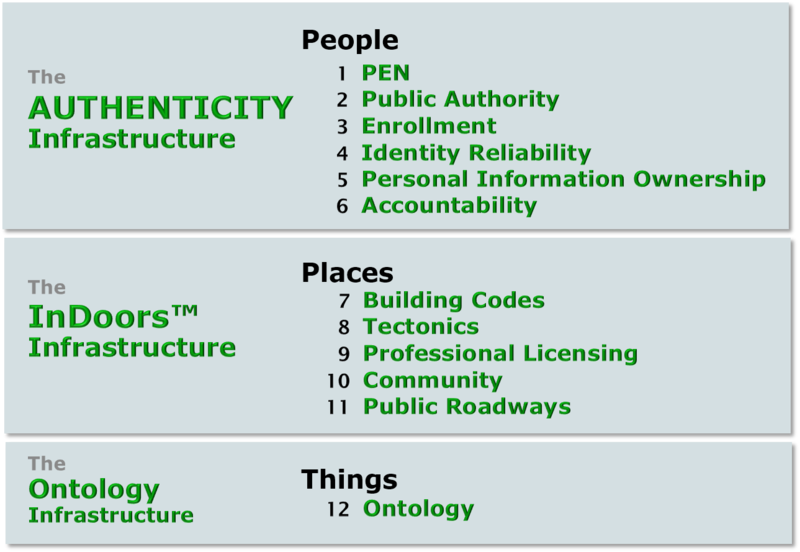
Twelve questions answered by the Twelve Components of the Quiet Enjoyment Infrastructure
PEOPLE: The Authenticity Infrastructure
The PEN™ component (Personal Endorsement Number)
answers this question:
Question: Authenticity calls for pervasive digital signatures by reliably identified human beings. How do you protect the PENs (private keys), while making them available for digital signatures?
Answer: Nothing we do with computers, phones, tablets, or other information appliances will be secure until there is a sound way to keep files, directories, identifiers, and other important items in a truly protected space. That in turn requires isolation of PENS (private keys), as specified in the PEN Component.
The PUBLIC AUTHORITY component
answers this question:
Question: Reliable digital identity certificates, professional licenses, and occupancy permits call for a reliable source of issuing public authority that is independent of any geographic jurisdiction. Where do we find such a source of duly constituted global public authority?
Answer: On March 7, 2005, the City of Osmio was chartered at the Geneva headquarters of the oldest international governance body in the world, the International Telecommunication Union. On that day, Osmio inherited the goals of the ITU’s recently terminated PKI - called the World e-Trust Initiative - and at the same time became completely independent of the ITU.
The ENROLLMENT component
answers this question:
Question: How do you establish identity in the first place?
Answer: Enrollment can be costly or not, depending upon the level of rigor needed by relying parties. The ENROLLMENT Component ensures that evidence supporting a claim of identity is gathered properly for the requisite level of rigor and presented along with the PCN (public key) in a certificate signing request(CSR) to the Osmio Vital Records Department (VRD).
The IDENTITY RELIABILITY component
answers this question:
Question: When someone identifies themself to you, how do you know how reliable is that claim of identity?
Answer:The foundational identity certificate is accompanied by other certificates and by an identity quality record. Very little might be revealed to a relying party about the person identified other than their identity quality information and the fact that the identity certificate has not been revoked. Despite that anonymity, the Identity Reliability Component establishes accountability.
The PERSONAL INFORMATION
OWNERSHIP component
answers this question:
Question: Personal control of information about oneself has been a long-sought goal of privacy activists. How can a universal identity credential restore privacy rather than erode it even further?
Answer:The foundation of real privacy is your own control over information that identifies you. Without such strong controls, individuals will rightfully resist the idea of a strong identity infrastructure. While the companies that accumulate information about you regard that information as their own corporate asset, the PIOC provides technological and legal tools by which you can reclaim that asset as your own personal property. property. The PIOC uses accountable anonymity, letting you assert your identity without disclosing your identity.
The ACCOUNTABILITY component
answers this question:
Question: We value anonymity, but at the same time we want others to be accountable. What happens when someone whose privacy is protected anonymously harms me, my community, or my country?
Answer:As QEI must protect your privacy, it must also protect your right to recourse if you are harmed by someone whose privacy is similarly protected. Law enforcement must also be able to seek a court order to intercept communications when a legitimate court deems it necessary to protect public safety. The Accountability Component ensures that due process prevails even in jurisdictions that are not known for adherence to due process.
PLACES:The InDoors™ Infrastructure
The BUILDING CODES component
answers this question:
Question: By what standards are we assured that an information facility is habitable — that is, secure and manageable?
Answer:Your information is never secure in a private, cryptographic tunnel if it is exposed at the ends of the tunnel. Indeed, a tunnel can be less secure than the outdoor space around it, because it gives its occupants a false sense of security. Building codes are sets of standards and procedures that ensure the integrity of the virtual buildings that enclose, for example, the ends of tunnels.


The TECTONICS component
answers this question:
Question: How do we bring the benefits of InDoor™ spaces to our computers, tablets, phones, and other devices?
Answer:Established operating systems are invitations to plantation owners to help themselves to the contents of your information home. With the new "continents," we will exchange the vulnerable and cranky old operating system foundation in computers and phones for a more reliable, secure, and manageable set of foundations for places rather than “apps.” Montaigne, Dorren, and Glenda are continents.
The PROFESSIONAL LICENSING component
answers this question:
Question: Who decides whether a facility is habitable — that is, that it conforms to building codes? How do we apply the methods used in answering that question to answer other procedural questions?
Answer:As with physical real estate, our bounded online spaces need qualified architects, contractors, property management people and building inspectors to ensure that they serve our purposes. The Professional Licensing Component provides a system of certification of their professional credentials and of the results of their work. The Professional Licensing Component does the same for the attestation profession and for other professions as well.
The COMMUNITY component
answers this question:
Question: How do we bring privacy and authenticity to social media?
Answer: Where are these online buildings built? Who owns them? Who pays for them? How do they connect to each other in a rational way? How does online real estate become economically sustainable — that is, profitable? We find our answer in the surprising intersection between skills and methods in the media industry and those of the urban planning profession.
The PUBLIC ROADWAYS component
answers this question:
Question: Can the outdoor public transport system also benefit from QEI?
Answer:The roadway system, the Internet, is far ahead of the real estate — the secure online places where people can safely gather. Its protocols, like those for the next generation of concrete Interstate highways, are well established. But the facilities that control the Internet are entirely too vulnerable to criminals and vandals. Access controls based upon measurably reliable identities must be put in place.
PLACES:The InDoors™ Infrastructure
The ONTOLOGY component
answers this question:
Question: Strict definitions of terms reduces confusion in the world of building codes and permits. Can terminology standards reduce rampant “FUD factor” confusion in information technology?
Answer: What information technology provides to the online world is no more mysterious than what architects, contractors, and property managers provide to the physical world. The Ontology Component requires the use of standardized terminology in the permitting of new facilities. By using the well-understood language of real estate, management can finally direct information technology, rather than the other way around.



