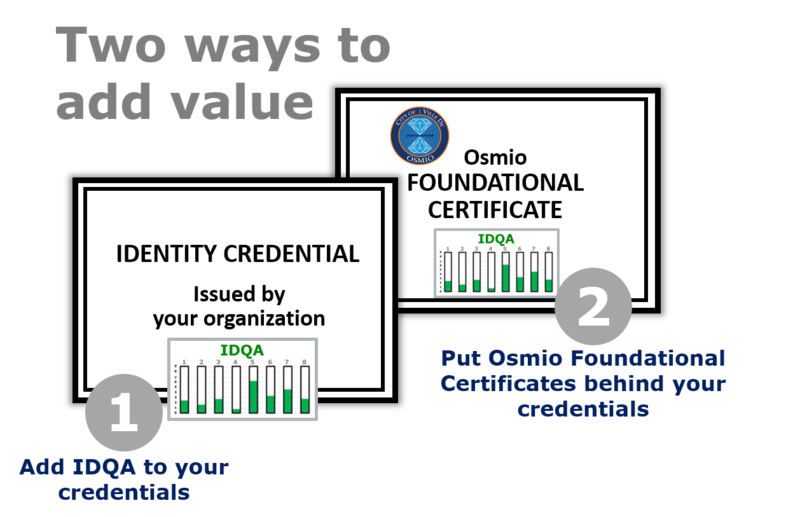
Add value to your credential
If your organization is involved in the issuance of identity credentials, let Osmio add value to those credentials in either of two ways:
- The Osmio Identity Quality Assurance (IDQA™) Program
- The Osmio Foundational Certificate with IDQA™
The relying parties in your identity federation trust your technology — they trust that identity assertions are handled properly. But to what extent do they trust the assertions themselves? How sure can they be that Mary Jones is really Mary Jones and not an impostor?
Whether you apply IDQA™ directly to your own credential, or you put an Osmio Foundational Certificate behind your credential, you’ll give relying parties (including your own organization) an unmatched level of assurance that users are who they claim to be.
 The Osmio Identity Quality Assurance (IDQA™) Program
The Osmio Identity Quality Assurance (IDQA™) Program
When you apply IDQA directly to your own credential, you’ll give relying parties (including your own organization) an unmatched level of assurance that users are who they claim to be.
 The Osmio Foundational Certificate with IDQA™
The Osmio Foundational Certificate with IDQA™
When you put an Osmio Osmio Foundational Certificate behind your credential, you’ll give relying parties (including your own organization) an unmatched level of assurance that users are who they claim to be.
The Osmio VRD (Vital Records Department) Foundational Certificate is an x.509v3 PKI digital identity certificate that functions as a digital birth certificate. Like a paper birth certificate, it is backed by duly constituted public authority. The City of Osmio, which was chartered on March 7, 2005, at the Geneva headquarters of the International Telecommunication Union, an agency of the United Nations, is the attesting authority.
How IDQA™ adds value to your credential
While there exists an abundance of commercial identity verification services, only Osmio is prepared to assemble the output of those services along with other Evidence of Identity (EOI) to provide a permanent attestation of the level of confidence that you or your relying parties can have in a claim of identity.
Osmio and its agents, including Attestation Officers and Authorized Agencies, will provide a program of Identity Quality evaluation for all holders of your identity credentials.
With IDQA, the strength of a user’s identity claim — its Identity Quality — is evaluated using eight metrics, with each metric measured on a scale of zero to nine. All eight scores are then added together, giving an aggregate Identity Quality score of zero to seventy-two.
Relying parties (including your own organization) can set a minimum aggregate score, or minimums of any of the eight component scores, to grant or deny access to a resource.
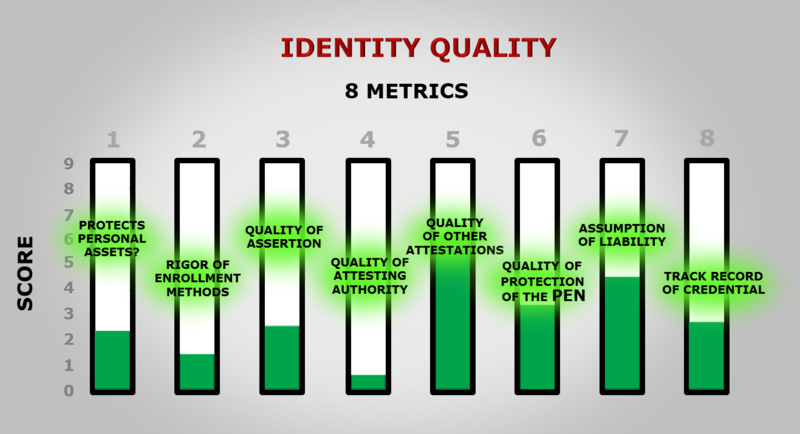
The eight metric scores added together give an Identity Quality score of 0-72
How IDQA scores are used
The eight scores are added together for an aggregate Identity Quality score of 0 to 72.
Whenever and wherever the credential is presented, the aggregate Identity Quality score and its eight component scores are presented, letting the relying party know the degree to which the identity claim can be relied upon.
Assignment of lower IDQA scores is done in an automated fashion, while the higher scores are assigned by a human Attestation Officer, as described previously in the Enrollment Component.
Some applications require more assurance of the validity of the identity claim than others. And some require different types of assurance. An online commercial real estate auction will want a high degree of assumption of liability (metric #7), while a social network for children will want to see that the user was enrolled in a face-to-face setting, establishing a high enrollment quality score (metric #2).
IDQA score inherited from Foundational Certificate
Most of the eight measures of identity quality of any puzzle kit are inherited directly from the Foundational Certificate, which ideally is a Digital Birth Certificate whose PEN (private key) signed the certificate signing request (CSR) of the utility or device certificate used in the everyday credential. However, everyday credentials can carry their own IDQA score. In fact, a credential’s IDQA score applies only to the actual certificate and the card, token, hard drive or other device that houses it.
The eight metrics of Identity Quality™ Each scored on a scale of 0-9
-
Degree of protection of personal assets
Does the user have "skin in the game" or are your organization’s assets the only ones at risk? If the only reliable way to prevent credential sharing is to use credentials that protect the user's financial, reputational, and identity assets, then to what extent does the identity protect those personal assets? Ownership of the credential itself is considered in this score.
-
Quality of enrollment practices
What type of enrollment procedure was used? Did it involve PII corroboration (“KBA”)? Was it face-to-face notarial or remote? How is provisioning performed? How is the process supervised and audited? How many eyes are watching? Each risk profile and highest protected digital asset value will call for a particular enrollment procedure.
-
Variety of means of assertion
Does the credential support FIDO, OpenID, i-Name, Shibboleth, CardSpace? Does it use SAML assertions? A well-used identity is a more reliable identity; the more places it is used the better.
-
Quality of authoritative attestation
What source of authority attests to the validity of the assertion — that is, the claimed identity? Is the attesting party a certification authority? How reliable are their attestation practices? How is identity status reported: CRL, OCSP, or another method?
-
Self-sovereign EOI and attestation from others
To what extent does the “complex relational web” of self-sovereign methods support the subject’s claim of identity, and to what extent do colleagues, employers, and sources of other relationships corroborate the subject's claim of identity? The more acquaintances who are willing to back up the subject’s claim of identity, and the higher the scores of those who do so, the higher this score will be.
-
Quality of the credential
What are the characteristics of the credential and its carrier? Is one key pair used for everything, or are different key pairs or simple serial numbers used for different applications? The carrier of the credential is equally important. Some risk-profile/asset-value situations call for two-, three-, or four-factor hardware tokens or a one-time password, while a soft credential in the client computer or even a record in a directory will suffice for others.
-
Quality of assumption of liability
If fraud is committed with the use of the credential, who carries the liability? Is that commitment bonded? What are the terms of the bond? What is the source of funds for fulfillment of the bond? Are there caveats or is the commitment absolute, regardless of the circumstances that made the credential available to the perpetrator? To protect assets and processes of the highest value, where a compromised identity would have the most serious consequences, there should be both civil and criminal liability involved in the issuance and ongoing use of the credential. Equally important is protection against fraudulent repudiation. Non-repudiation is perhaps the most difficult goal for a trust system to achieve, but it is necessary for the system to be useful to relying parties where significant transactions are involved.
-
Reputation of the credential
How long has the credential been used without revocation or reported compromise? How many transactions and authentication events has it been used for in total? The longer a credential has been used without incident, the more reliable it tends to be. Note that the reputation of the credential is not the same thing as the reputation of the person. For example, if someone with a very good reputation has a habit of lending his or her credential to family members and colleagues — resulting in documented confusion over who is responsible for what — then the reputation of the credential is greatly diminished.


